Aniar Blog
Cybercrime has gotten a lot scarier as the methods have become more sophisticated and difficult to detect. They might look like official business, but in reality, they are dangerous and well-thought-out attacks that can endanger your company and all those who work for it. Today, we want to break down some of the ways these cyberthreats can fool even the most cautious employees.
Every day, cybercriminals wake up and choose violence.
Whether it’s a nasty strain of ransomware demanding a king’s ransom or a sneaky little virus that just wants to watch your business burn, the threats never stop coming. That’s why locking down your business is as essential as putting cream in your morning coffee.
Everywhere you look on the Internet, there’s a scam, threat, or other malicious entity.
Okay, maybe that’s not 100% true, but the possibilities are nearly endless for hackers. They’ll hide spyware, adware, and even ransomware online, so you must take measures to ensure that your devices and business are safe.
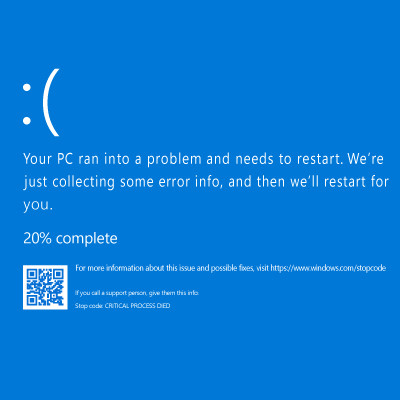
July 18th, 2024 saw one of the most widespread and devastating outages in recent memory, as a global update from cybersecurity company CrowdStrike brought about significant impacts to major infrastructures and societal needs. All this occurred even though only 1% of Windows operating systems experienced the issue.
Every year, there seems to be a notable increase in high-profile ransomware attacks. If you haven't yet devised a plan to shield your business from these dangers, the time to act is now. Luckily, there are proactive steps you can take to reduce the impact of ransomware attacks, and it all starts with preparation.
For the most part, Microsoft takes security as seriously as it should, issuing updates and patches to maintain your Windows and Server operating systems. While you can count on receiving these updates for your supported operating systems, what you might not have known is that Microsoft accidentally overlooked a flaw in its own defenses.
Smartphones have managed to hold out against ransomware a bit longer than other hardware and operating systems, but those days are coming to an end. It’s important to remember that the average smartphone is not protected with antivirus software and thus remains threatened by your standard ransomware attacks. It is absolutely critical that your business doubles down on its protection against ransomware, especially in the mobile market.
We all know at this point how dangerous ransomware can be for businesses. It can lock down files, threaten operational continuity, and in some cases subject victims to brutal fines as a result of privacy breaches. One place where you might not expect ransomware to hit, however, is customer reviews, and it all stems from the big question: do you pay to resolve a ransomware attack or not?
Do you ever see an advertisement for a free download of a popular Windows application and think, “Wow, this sure sounds too good to be true!”? Well, it most definitely is, and hackers use these malvertisements to infect computers with malware and other threats. Specifically, malvertising is used to download three different types of malware, all of which can cause harm to unwary businesses.
Network security is challenging for many businesses, and it’s largely because of the large number of various threats that populate the Internet. Some companies simply don’t know what the correct measures to take are, leaving themselves vulnerable to these threats on both a security standpoint and an employee training standpoint. We’ll delve into some of these threats and how they can be addressed.
You’d think that cybercriminals would use ransomware to target high-profile businesses with loads of money to extort, but this is not always the case. Even a small business can fall victim to these particularly devastating threats. Ransomware, just like other threats out there, has continued to evolve and adjust its approaches based on the current cybersecurity climate, so what are some of the latest developments in ransomware?
Ransomware is bad stuff, and it’s only gotten worse with its recent resurgence that aligned with the COVID-19 pandemic. Phishing attacks and other means by which ransomware is commonly spread have used the current atmosphere as a springboard. This makes it even more critical that these kinds of behaviors and attempts can be spotted and stopped.
With so many high-profile ransomware attacks being launched against manufacturers, pipelines, and even hospitals, it’s no surprise that many companies are worried about what the future of this threat means for their organizations. Ransomware poses a serious threat, one that cannot possibly be ignored, so we urge you to take action now so you don’t come to regret it later.
Network security isn’t just for large, high-profile enterprises; even small businesses need to take it seriously. All businesses have something of value to hackers, and if you don’t believe this is the case for your organization, think again. All data is valuable to hackers, and you need to do everything in your power to protect it—especially against threats like Agent Tesla, the latest version of phishing malware designed to steal your data.
It’s no secret that software often does not work as intended. Developers frequently discover bugs and patch them out. The same can be said for security vulnerabilities. Despite the importance of these updates, small businesses often fail to implement these patches and updates in a timely manner, a practice which can lead to more problems down the road.
The situation surrounding the hack against Colonial Pipeline has only become more complex as new information has come to light, each new discovery providing more insights and potentially actionable takeaways. Let’s examine some of the biggest developments surrounding the attack, and what they will likely mean for overall cybersecurity from this point forward.