Aniar Blog
For computer enthusiasts one of the major questions has always been Mac vs. PC. Most people prefer one over the other, while some are fine using either. The problem with having two popular non-compatible computer systems is that they each use proprietary file types. For documents, the answer was developed by Adobe: the PDF. Today, we’ll take a look at Portable Document Format.
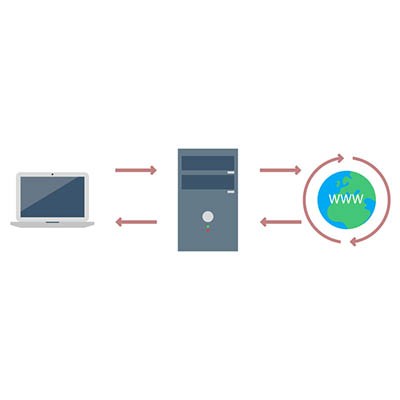
Your server room may be somewhat intimidating to consider. Wires everywhere, mechanical boxes that just sit there, lights blinking intermittently, and the distinct feeling that you probably shouldn’t touch anything - not even a proxy server, whatever that is. However, to help you get to know your tech, the proxy server is exactly what we discuss below!
You see the term “social media” thrown around all the time, but what does it mean for both individual users and whole businesses? Organizations that understand the importance of social media have a unique advantage over other businesses in the same industry, be it a way to attract more consumers or a way to protect against common security threats that find their home on these websites.
Security is a necessity. Every technology professional will tell you this, but in an age where employees are taking information on the go, it’s trickier than it’s ever been before. Encryption is one of the ways that businesses are attempting to shore up their security, but this also requires having an encryption key. This week’s technology term is all about encryption, as well as how encryption keys protect your business’ data.
If you are trying to identify a specific issue with your PC, it can be difficult to do so due to the fact that there are so many moving parts in an operating system. Still, you want a secure way to find the problem and diagnose it. Thankfully, Safe Mode allows you to take a look at your computer in its most basic form to see what the root of the issue is.
Marketing is increasingly critical to a business’ success, especially when it comes to the use of content as an impressions generator. This makes it all the more important for your content to be well organized and managed. Here, we’ll go over a few options you have as far as content management systems are concerned, and how they make maintaining your content strategy that much simpler.
If you hang out around technology professionals for any period of time, chances are that you’ve heard the word “cache” used before. The word, pronounced cash, is usually heard in the phrase, “clear the cache,” but if you don’t know what this phrase means, how can you benefit from it? Since this week’s tech term is “cache,” let’s get into the details.
Pop culture gives us an impression of what cyber investigations look like. Official-looking people, in impeccable suits, typing away at terminals and analyzing the data scrolling past them on their heads-up displays. In reality, computer forensics (as they are actually called) are a little less dramatic, and much more serious. For today’s tech term, we’ll dig into the field of computer forensics.
Inside its casing, your computer contains many parts. While these parts may not be moving, they are hard at work, enabling you to use your computer to accomplish your goals. For today’s Tech Term, we’ll take a closer look at just one, the motherboard, and examine what it contributes to your device’s operation.